A satellite is an object that revolves around another object. For example, earth is a satellite of The Sun, and moon is a satellite of earth.
A communication satellite is a microwave repeater station in a space that is used for telecommunication, radio and television signals. A communication satellite processes the data coming from one earth station and it converts the data into another form and send it to the second earth station.
How a Satellite Works
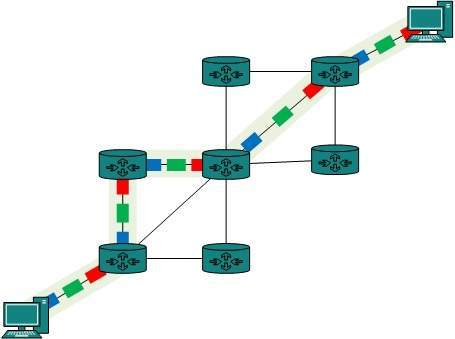
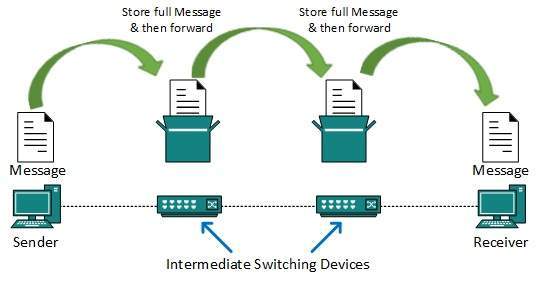
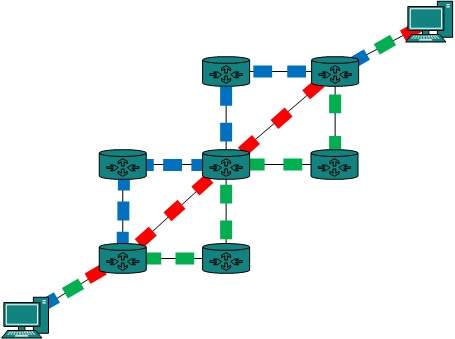
Two stations on earth want to communicate through radio broadcast but are too far away to use conventional means. The two stations can use a relay station for their communication. One earth station transmits the signal to the satellite.
Uplink frequency is the frequency at which ground station is communicating with satellite. The satellite transponder converts the signal and sends it down to the second earth station, and this is called Downlink frequency. The second earth station also communicates with the first one in the same way.
Advantages of Satellite
The advantages of Satellite Communications are as follows −
- The Coverage area is very high than that of terrestrial systems.
- The transmission cost is independent of the coverage area.
- Higher bandwidths are possible.
Disadvantages of Satellite
The disadvantages of Satellite Communications are as follows −
- Launching satellites into orbits is a costly process.
- The bandwidths are gradually used up.
- High propagation delay for satellite systems than the conventional terrestrial systems.
Satellite Communication Basics
The process of satellite communication begins at an earth station. Here an installation is designed to transmit and receive signals from a satellite in orbit around the earth. Earth stations send information to satellites in the form of high powered, high frequency (GHz range) signals.
The satellites receive and retransmit the signals back to earth where they are received by other earth stations in the coverage area of the satellite. Satellite's footprint is the area which receives a signal of useful strength from the satellite.
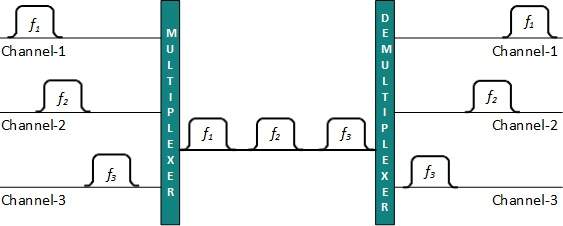
The transmission system from the earth station to the satellite through a channel is called the uplink. The system from the satellite to the earth station through the channel is called the downlink.
Satellite Frequency Bands
The satellite frequency bands which are commonly used for communication are the Cband, Ku-band, and Ka-band. C-band and Ku-band are the commonly used frequency spectrums by today's satellites.
It is important to note that there is an inverse relationship between frequency and wavelength i.e. when frequency increases, wavelength decreases this helps to understand the relationship between antenna diameter and transmission frequency. Larger antennas (satellite dishes) are necessary to gather the signal with increasing wavelength.
Earth Orbits
A satellite when launched into space, needs to be placed in certain orbit to provide a particular way for its revolution, so as to maintain accessibility and serve its purpose whether scientific, military or commercial. Such orbits which are assigned to satellites, with respect to earth are called as Earth Orbits. The satellites in these orbits are Earth Orbit Satellites.
The important kinds of Earth Orbits are −
- Geo-synchronous Earth Orbit
- Geo-stationary Earth Orbit
- Medium Earth Orbit
- Low Earth Orbit
Geo-synchronous Earth Orbit (GEO) Satellites
A Geo-synchronous Earth orbit Satellite is one which is placed at an altitude of 22,300 miles above the Earth. This orbit is synchronized with a side real day(i.e., 23hours 56minutes). This orbit can have inclination and eccentricity. It may not be circular. This orbit can be tilted at the poles of the earth. But it appears stationary when observed from the Earth.
The same geo-synchronous orbit, if it is circular and in the plane of equator, it is called as geo-stationary orbit. These Satellites are placed at 35,900kms (same as geosynchronous) above the Earth’s Equator and they keep on rotating with respect to earth’s direction (west to east). These satellites are considered stationary with respect to earth and hence the name implies.
Geo-Stationary Earth Orbit Satellites are used for weather forecasting, satellite TV, satellite radio and other types of global communications.
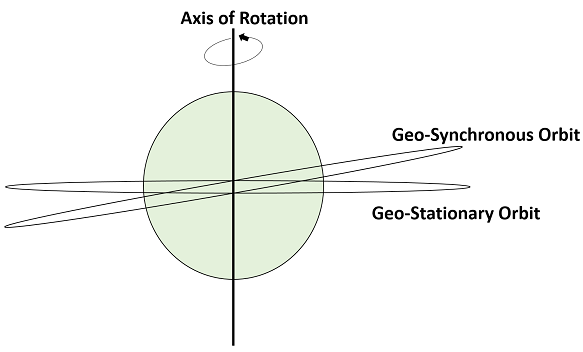
The above figure shows the difference between Geo-synchronous and Geo- Stationary orbits. The Axis of rotation indicates the movement of Earth.
The main point to note here is that every Geo-Stationary orbit is a Geo-Synchronous orbit. But every Geo-Synchronous orbit is NOT a Geo-stationary orbit.
Medium Earth Orbit (MEO) Satellites
Medium earth orbit (MEO) satellite networks will orbit at distances of about 8000 miles from earth's surface. Signals transmitted from a MEO satellite travel a shorter distance. This translates to improved signal strength at the receiving end. This shows that smaller, more lightweight receiving terminals can be used at the receiving end.
Since the signal is travelling a shorter distance to and from the satellite, there is less transmission delay. Transmission delay can be defined as the time it takes for a signal to travel up to a satellite and back down to a receiving station.
For real-time communications, the shorter the transmission delay, the better will be the communication system. As an example, if a GEO satellite requires 0.25 seconds for a round trip, then MEO satellite requires less than 0.1 seconds to complete the same trip. MEOs operates in the frequency range of 2 GHz and above.
Low Earth Orbit (LEO) Satellites
The LEO satellites are mainly classified into three categories namely, little LEOs, big LEOs, and Mega-LEOs. LEOs will orbit at a distance of 500 to 1000 miles above the earth's surface.
This relatively short distance reduces transmission delay to only 0.05 seconds. This further reduces the need for sensitive and bulky receiving equipment. Little LEOs will operate in the 800 MHz (0.8 GHz) range. Big LEOs will operate in the 2 GHz or above range, and Mega-LEOs operates in the 20-30 GHz range.
The higher frequencies associated with Mega-LEOs translates into more information carrying capacity and yields to the capability of real-time, low delay video transmission scheme.
High Altitude Long Endurance (HALE) Platforms
Experimental HALE platforms are basically highly efficient and lightweight airplanes carrying communications equipment. This will act as very low earth orbit geosynchronous satellites.
These crafts will be powered by a combination of battery and solar power or high efficiency turbine engines. HALE platforms will offer transmission delays of less than 0.001 seconds at an altitude of only 70,000 feet, and even better signal strength for very lightweight hand-held receiving devices.
Orbital Slots
Here there may arise a question that with more than 200 satellites up there in geosynchronous orbit, how do we keep them from running into each other or from attempting to use the same location in space? To answer this problem, international regulatory bodies like the International Telecommunications Union (ITU) and national government organizations like the Federal Communications Commission (FCC) designate the locations on the geosynchronous orbit where the communications satellites can be located.
These locations are specified in degrees of longitude and are called as orbital slots. The FCC and ITU have progressively reduced the required spacing down to only 2 degrees for C-band and Ku-band satellites due to the huge demand for orbital slots.